Best Practices for Trezor Login | Trezor Login Security Tips | Trezor Login Safe Methods | How to Secure Your Trezor Login
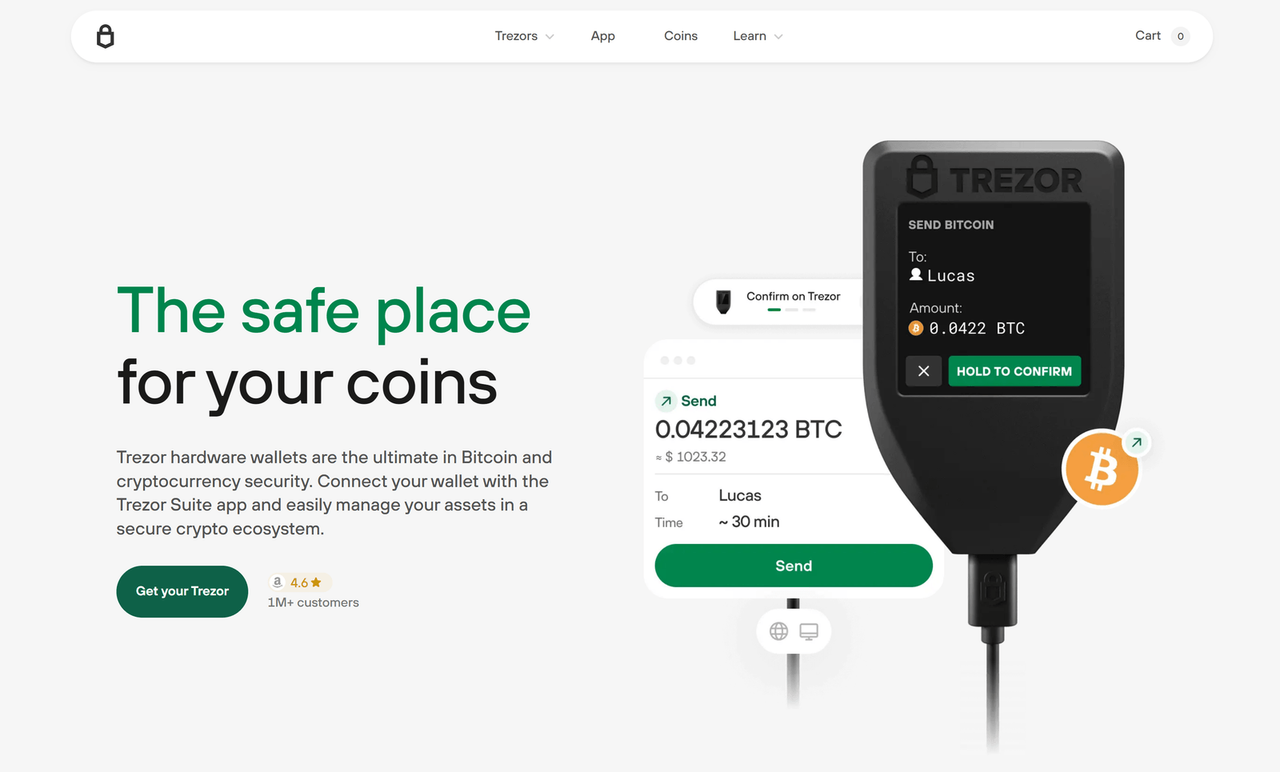
When it comes to managing cryptocurrency securely, knowing the best practices for Trezor login is essential. Whether you're a new user or a seasoned crypto investor, ensuring your Trezor login is secure, efficient, and private protects your digital assets from threats. This detailed guide covers Trezor login best practices, Trezor login tips, Trezor login methods, and how to make your Trezor login safe and secure across all devices.
In the cryptocurrency world, security starts with your Trezor login process. Whether accessing Trezor Suite, using Trezor Bridge, or interacting with third-party wallets, applying secure Trezor login practices ensures that your coins stay safe.
Made in Typedream